- Comms
- Law
- Medic
- News
- Opinion
- Threat Watch
- Training
- Warrior Tools
- Accessories
- Ammo
- Body Armor
- Books
- Clothing
- Commo
- Gear
- Handguns
- Holsters
- Knives
- Long Guns
- ACC
- Accuracy International
- Barrett
- Benelli
- Beretta
- Blaser
- Bushmaster
- Custom
- CZ
- Desert Tactical Arms
- DPMS
- FN
- Forums
- HK
- IWI
- Kel-Tec Long Guns
- LaRue
- LWRC
- McMillan
- Mosin Nagant
- Mossberg
- Para
- Remington
- Rock River Arms
- Ruger Long Guns
- Sabre Defense
- Sako
- SIG Sauer
- SKS
- Smith & Wesson Long Guns
- Springfield
- Styer
- Weatherby
- Wilson Combat
- Winchester
- Magazines
- Maintenance
- Navigation
- Optics
- Sights
- Tech
- Warriors
Archive for category Comms
Taming Chaos with a Personal Plan
Posted by Brian in Comms, Opinion, Threat Watch on 17/Mar/2011 14:53
Taming Chaos with a Personal Plan is republished with permission of STRATFOR.
By Scott Stewart
Over the past week we’ve seen a massive earthquake and tsunami in Japan that caused a nuclear accident, the Saudis sending troops into Bahrain to quell civil unrest there and the government of Yemen taking measures to expel foreign media as protests have swelled against Yemeni President Ali Abdullah Saleh.
We have also recently seen large-scale evacuations of expatriates from Tunisia, Egypt and Libya, and it is not unreasonable to assume that we might see a similar exodus from Bahrain and Yemen if developments in those countries deteriorate. Moreover, in Japan, the risk of radiation and conditions that are not yet under control at the Fukushima Daiichi nuclear power plant could force further evacuations there.
In light of this uncertain environment, STRATFOR thought it prudent to address once again the topic of personal contingency planning. Indeed, we also made this topic the subject of this week’s  Above the Tearline video. While we have often discussed this topic in relation to terrorist attacks, its principles are also readily applicable to crises caused by natural disaster, war and civil unrest. When a crisis erupts, having an established personal contingency plan provides people with a head start and a set of tools that can help them avoid, or at least mitigate, the effects of the chaos and panic that accompany crisis events. Read the rest of this entry »
Above the Tearline video. While we have often discussed this topic in relation to terrorist attacks, its principles are also readily applicable to crises caused by natural disaster, war and civil unrest. When a crisis erupts, having an established personal contingency plan provides people with a head start and a set of tools that can help them avoid, or at least mitigate, the effects of the chaos and panic that accompany crisis events. Read the rest of this entry »
Using the Evolved Cyber Range – Free Webinar
Posted by Gary in Comms, Threat Watch, Training on 11/Mar/2011 19:04
From: IDGA
Using the Evolved Cyber Range to Arm and Train U.S. Warriors to Win Cyber War
Tuesday, April 5, 2011, 2:00 PM – 3:00 PM ET
Presenter:Â Scott Register
How are military and intelligence organizations such as the U.S. Defense Information Systems Agency (DISA), the U.S. European Command (EUCOM), and Northrop Grumman (U.S. and U.K.) deploying cyber range technology? What are these organizations doing to develop the expertise of personnel and then equipping them with the advanced tools needed to fulfill cyber security missions?
Join BreakingPoint Systems, the global leader in cyber range technology, and learn how U.S. government and military can properly train personnel with the skills to defend against cyber terrorism, espionage, and theft of intellectual property.
Listen to the best practice case studies of DISA, EUCOM, and Northrop Grumman as they use the latest technology and establish a turnkey system to deliver a complete, scalable, and operational cyber range.
Learn how to use technology to simulate Internet-scale cyber war conditions in a controlled environment in order to establish IT certification methods and curriculum needed for assessing, training, and qualifying cyber warrior personnel.
After attending this webinar you will know how to:
- Deploy and use a modern cyber range machine to create an operationally relevant environment that precisely mirrors the Global Information Grid (GIG), enabling sophisticated simulation of real-world cyber conditions
- Optimize and harden the resiliency—the performance, stability, and security—of next-generation deep packet inspection (DPI) devices to carry out effective Lawful Intercept programs and related missions
- Model and research advanced cyber threats including Stuxnet and botnet-driven distributed denial of service (DDoS) attacks
- Implement a scalable approach for training and certifying cyber warriors in critical Information Assurance (IA), Information Operations (IO), and Mission Assurance (MA) skills.
- Establish centralized command and control to monitor and manage a distributed network of remote cyber ranges
Complimentary Training for CISSP and Security Clearance
From: University of Fairfax
Federal agencies and contractors need CISSP certified and cleared cyber security professionals. Don’t miss out! Earn your CISSP and get your Security Clearance in 2011 and watch your cyber security career take off! Attend a complimentary:
– CISSP Exam Prep Clinic and
– Security Clearance Workshop
at GOVSEC 2011 Thursday March 31, 2011. Seating is limited…
Sophisticated Attacks Threaten Major Energy Firms
Posted by Gary in Comms, Threat Watch on 18/Feb/2011 15:29
From: Dark Reading
New advanced persistent threat (APT) attack combines a variety of vectors, seeks to steal sensitive data, McAfee researchers say
By Tim Wilson
Researchers at McAfee yesterday revealed details of a new advanced persistent threat attack that uses a combination of methods in an effort to steal sensitive operations, exploration, and financial data from petroleum and energy companies.The new series of attacks, dubbed “Night Dragon,” may have begun as long ago as 2008, McAfee says in its report about the threat. “Now, new Night Dragon attacks are being identified every day,” the report says. Night Dragon’s creators “appear to be highly organized and motivated in their pursuits,” McAfee says.The attack is “a combination of social engineering and well-coordinated, targeted, cyber attacks using Trojans, remote control software, and other malware.” The report says McAfee has seen evidence of the attacks in virtually every region of the globe, and that it has “identified tools, techniques, and network activities utilized … that point to individuals in China as the primary source. ”
Electromagnetic Warfare
The Navy is in the process of replacing old EA-6B Prowlers with new EA-18G Growlers (a electronic warfare version of the Super Hornet).
Via Wired’s Danger Room blog:
The frontline weapon for this electronic war is a new airborne jamming system currently in development. The Next Generation Jammer should allow the Navy to blind the enemy’s radars, disrupt its communications and slip malicious code into computer networks.
Besides radar-jamming, the NGJ should allow the Navy to disable remotely detonated, improvised explosive devices — something the EA-6B already does — as well as insert viruses into command networks, a tactic Israel allegedly first used in combat during its 2007 air attacks on a suspected Syrian nuke site.
FAA to pilots: Expect ‘unreliable or unavailable’ GPS signals
Posted by Jack Sinclair in Comms, News on 20/Jan/2011 22:40
Unspecified Pentagon ‘tests’ cited
“The US Federal Aviation Administration is warning pilots to expect “unreliable or unavailable†signals from their global positioning gear as a result unspecified tests being carried out by the Department of Defense.
The Notice to Airmen, or NOTAM (PDF) said the GPS tests will be carried out beginning Thursday and are expected to last through February 22. They will cause spotty GPS signals in a several hundred mile radius centered off the coast of Florida.”
http://www.theregister.co.uk/2011/01/20/unavailabe_gps_warning/
Protect Your Smartphone
Over at ArsTecnica, a technology site, there is a good article about how and why you should want to protect the data on your smartphone. Here is a snippet:
Exhaustive cell phone searches aren’t exactly commonplace today, but they’re growing more and more frequent as law enforcement begins to realize how much incriminating information modern smartphones tend to contain. The rapidly growing digital forensics industry already offers a range of tools to law enforcement designed for pulling data off of mobile phones, and entire books have been written on such topics as the forensic analysis of the iPhone operating system.
Unfortunately, few consumer-grade smartphones support full device encryption. While there are numerous smartphone apps available for encrypting particular types of files, such as emails (i.e. NitroDesk TouchDown), voice calls (i.e. RedPhone), and text messages (i.e. Cypher), these “selective” encryption tools offer insufficient protection unless you’re confident that no incriminating evidence exists anywhere on your smartphone outside of an encrypted container.
Car Theft by Remote Control
Posted by Gary in Comms, Threat Watch on 9/Jan/2011 16:15
From: MIT
Car thieves of the future might be able to get into a car and drive away without forced entry and without needing a physical key, according to new research that will be presented at the Network and Distributed System Security Symposium next month in San Diego, California.
The researchers successfully attacked eight car manufacturers’ passive keyless entry and start systems—wireless key fobs that open a car’s doors and start the engine by proximity alone.
China and its Double-edged Cyber-sword
Posted by Brian in Comms, Threat Watch on 10/Dec/2010 09:25
China and its Double-edged Cyber-sword is republished with permission of STRATFOR.
By Sean Noonan
A recent batch of WikiLeaks cables led Der Spiegel and The New York Times to print front-page stories on China’s cyber-espionage capabilities Dec. 4 and 5. While China’s offensive capabilities on the Internet are widely recognized, the country is discovering the other edge of the sword.
China is no doubt facing a paradox as it tries to manipulate and confront the growing capabilities of Internet users. Recent arrests of Chinese hackers and People’s Liberation Army (PLA) pronouncements suggest that China fears that its own computer experts, nationalist hackers and social media could turn against the government. While the exact cause of Beijing’s new focus on network security is unclear, it comes at a time when other countries are developing their own defenses against cyber attacks and hot topics like Stuxnet and WikiLeaks are generating new concerns about Internet security.
One of the U.S. State Department cables released by WikiLeaks focuses on the Chinese-based cyber attack on Google’s servers that became public in January 2010. According to a State Department source mentioned in one of the cables, Li Changchun, the fifth highest-ranking member of the Communist Party of China (CPC) and head of the Party’s Propaganda Department, was concerned about the information he could find on himself through Google’s search engine. He also reportedly ordered the attack on Google. This is single-source information, and since the cables WikiLeaks released do not include the U.S. intelligence community’s actual analysis of the source, we cannot vouch for its accuracy. What it does appear to verify, however, is that Beijing is regularly debating the opportunities and threats presented by the Internet. Read the rest of this entry »
Cyber-Threat Whitepapers
Posted by Gary in Comms, Threat Watch on 9/Dec/2010 14:31
Cyber Warfare
Posted by Gary in Comms, Threat Watch on 8/Dec/2010 17:07
From IDGA
Over the last year there have been multiple instances of breaches in cyber security in the DoD and government. Most recently a report detailing the fact that in April massive amounts of internet data traffic was re-routed through servers in China which then had access to the potentially sensitive information. The incident which lasted 18 minutes was traced back to China Telecom, a state owned telecommunications firm. The data included information from .mil and .gov sources as well as large corporations such as Microsoft and IBM.
It is not clear if any compromising information was gained from this effort or how or if any of the gathered data will be used. But it is concerning for many of the agencies and companies involved as they are unsure of where they stand or what could potentially be used against them in the future.
This is not an isolated incident and the U.S. government and the Pentagon have been battling cyber attacks, hacking, and other forms of internet crime for years now. However, in the last several years these attacks are growing in number and sophistication and are resulting in security breaches that could have grave consequences. Many seem to be coming from sources in Eastern Europe including Russia and an increasing number from China. However, it is unclear whether these attacks can be linked to government intelligence networks or are a result of cyber terrorists operating on their own personal agenda.
Net Centric Warfare Webinar
Posted by Gary in Comms, Threat Watch, Training on 29/Nov/2010 17:29
Coevolution of NCW: Challenges with Cyberspace and Organizational Development
This FREE webinar will be on:
Thursday, December 16, 2010, 2:00 PM – 3:00 PM ET
Presenter: Maj. Trisha Carpenter
The U.S. military is facing an entire new front in warfare, the cyber domain. Controlling and dominating this new technological theater is becoming critically important as U.S. Military leadership relies heavily on computer networks to communicate, gather INTEL, and even launch weapons and coordinated strikes. At the same time the military is striving to perfect the concept of Net Centric Warfare to effectively use technology to gain advantage and superiority over enemy forces. Two main obstacles may stand in the way of a successful transformation from the current haphazard state of cyberspace operations to a more productive future state required of Network Centric Warfare (NCW). The first obstacle is the military’s lack in knowledge of cyberspace operations. The second obstacle is the difficulty in understanding organizational change. This Webinar first presents a working definition of NCW to show how cyberspace and organizational change are related in the form of coevolution. It then discusses the organizational growth challenges faced by any organization operating in this domain, with a focus on the security missions likely to be given to cyber commands.
In this webinar participants will learn:
• An Operational Illustration of NCW
• Key Challenges in Cyberspace:
• Technical Environment: Cyber Triad
• Non-Technical Environment: Organizational Design
Zeus Trojan Targets Government and Military Workers
Posted by Gary in Comms, Threat Watch on 17/Nov/2010 17:38
From: Angela Moscaritolo
A new campaign of the password-stealing Zeus trojan is targeting workers from government and military departments in the United States and United Kingdom, according to security researchers at Websense. The trojan is being distributed through spoofed emails claiming to come from the U.S. National Intelligence Council. The bogus messages contain subject lines such as “Report of the National Intelligence Council.” The emails aim to lure users into downloading a document about the “2020 project,” which actually is Zeus. — AM
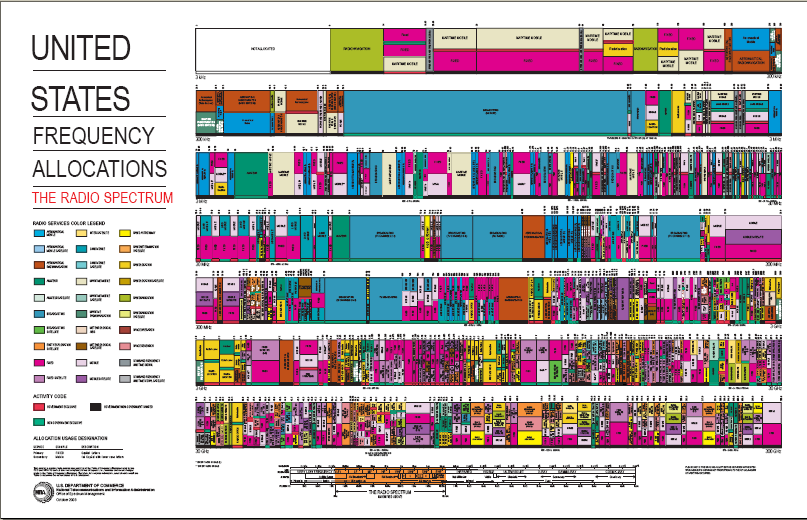
US Frequency Allocations – Radio Spectrum
US Frequency Allocations -Â The Radio Spectrum
From: NTIA Office of Spectrum Management
Graphic representation of frequency allocations in the United States – (PDF)
SOCOM Wants Android Devices
Posted by Brian in Comms, News, Warrior Tools on 1/Nov/2010 17:04
SOCOM wants to use Google’s Android devices instead of developing a proprietary system:
From Danger Room:
SOCOM calls it the Tactical Situational Awareness Application Suite, or TactSA, and it has to work in low-connectivity areas — the middle-of-nowhere places you’d expect to send the military’s most elite troops. It’s got to be peer-to-peer, encrypted “at the application level†and able to recover from “network outages and substantial packet loss.â€